Built for Trust, Secured for Scale
Athennian protects your most sensitive data with enterprise-grade encryption, robust platform controls and independent security certifications so your team can govern with confidence.
Meeting today’s security needs
Data Encryption & Access Control
Your data stays protected with enterprise-grade encryption and strict access controls, so only the right people have access, every time.
Platform & Infrastructure Security
Athennian’s secure AWS-hosted infrastructure and 24/7 monitoring keep your operations running safely, with resilience built in.
Trust &
Transparency
From third-party audits to real-time logging, Athennian gives you full visibility into your data, your activity and our security posture.
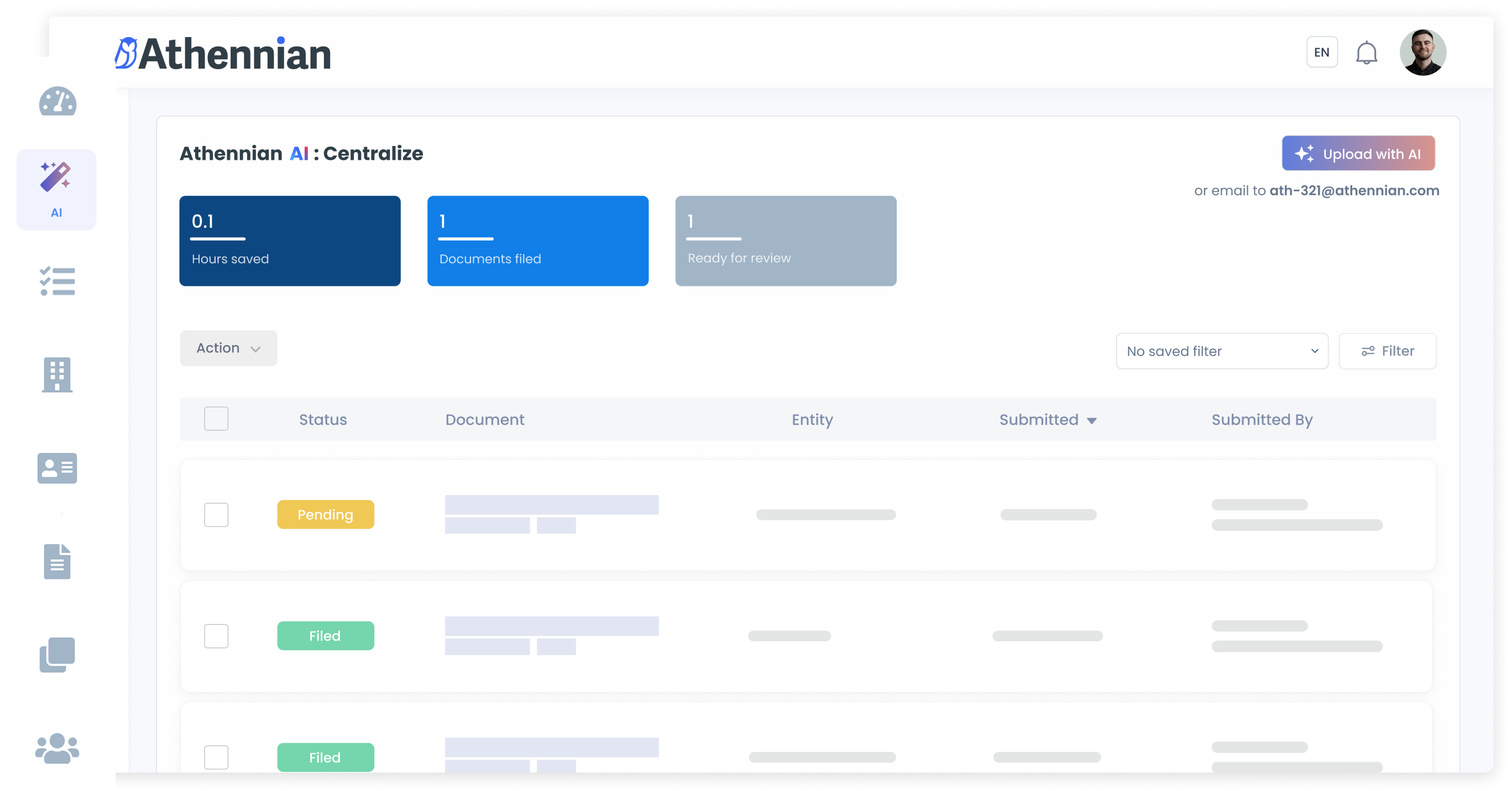
Certifications & Compliance
We adhere to rigorous security and privacy standards, validated by third parties, to help you meet your compliance obligations with confidence.

SOC 2 Type II
Athennian is SOC 2 Type II certified, confirming that our security, availability and confidentiality controls meet the highest standards as verified through independent third-party audits.
GDPR Compliant
We comply with the General Data Protection Regulation (GDPR) to protect the personal data and privacy of users across jurisdictions, including the EU and beyond.
Athennian Delivers
- End-to-end AES-256 and TLS 1.2+ encryption for data at rest and in transit
- Role-based access controls (RBAC) and multi-factor authentication (MFA)
- Single Sign-On (SSO) integration for streamlined, secure user access
- Secure, scalable cloud infrastructure powered by Amazon Web Services (AWS)
- Continuous network monitoring and intrusion detection systems
- Independent SOC 2 Type II certification and GDPR compliance
- Automated in-app audit logging for full transparency and traceability
- Regular third-party penetration testing and active bug bounty program
- Dedicated incident response protocols with rapid escalation and remediation
- Real-time security visibility through our Trust Dashboard
.svg)
Get a solid foundation for your governance ops
Talk to us about how Athennian can help your teams today.
Request a demo
Frequently Asked Questions
All customer data is encrypted both at rest and in transit. We use AES-256 encryption, the industry standard for data at rest, and TLS 1.2+ protocols to protect data in transit — ensuring that all information moving through our systems is secure from unauthorized interception or access.
Athennian adheres to AES-256 for stored data and TLS 1.2 or higher for data in transit, aligning with best practices in cloud-native data security.
Athennian is built with security as a foundational principle. Our application is hosted on Amazon Web Services (AWS), leveraging its robust infrastructure, including physical security, automated monitoring, and advanced threat detection.
We align with leading security frameworks, including the OWASP Top 10, and our platform undergoes regular penetration testing by certified third parties. Our internal security practices are modeled after NIST and ISO 27001 guidelines.
Yes. We support multi-factor authentication (MFA) to help prevent unauthorized access, and our platform includes role-based access controls (RBAC) to enforce appropriate permission levels across users and teams.
Infrastructure access is tightly controlled using a least privilege approach. Admin-level access is granted only to necessary personnel and is continuously audited.
Athennian is SOC 2 Type II certified, demonstrating that our controls around security, availability, and confidentiality are independently audited and meet the industry benchmark for service providers.
Yes. We work with independent auditors to conduct annual SOC 2 Type II audits and regularly engage external security partners to test and validate our controls and protocols.
We provide customers with detailed documentation on our security architecture, practices, and controls. Our team is available to answer technical and compliance-related questions, and we maintain an open, responsive stance toward security inquiries.
Absolutely. We make additional technical documentation and audit results available to customers and prospects upon request to support vendor due diligence, IT reviews, or compliance assessments.




-p-500.webp)
-p-500.webp)
-p-500.webp)
.webp)
